Adding exclusions in Windows Defender
If you are facing false positive issues in Windows Defender, you can add the file or folder in question to Windows Defender’s exclusion list. Windows Defender exclusions can also be useful in fixing some performance issues. Windows Defender does not play nicely with certain processes and slows them down significantly, process exclusions can help in unshackling these processes.
Ensure that the files are safe
Before adding a file to the exclusion list, you need to make sure that it is safe. You could give virustotal.com a try, to see what other Antivirus software thinks about the file. Please note that Virustotal should not be used for any file where privacy is a concern. Upload the file to Virustotal; they would test the file with multiple Antivirus software and show the test results. If you are convinced that the file is safe, you can add it to Windows Defender’s exclusions list as described below.
Steps
Launch Windows Security Center
Virus & threat protection ➾ Virus & threat protection settings ➾ Manage Settings ➾ Add or remove exclusions
Here you have the option to add a file, a folder, a process or a file type to the exclusion list. The exclude process option excludes all the files opened by the process from real-time protection; it does not exclude the process itself. Also, this exclusion does not apply to scheduled or other scans.
Wildcards
You can use wildcards like ? and * for defining file or folder exclusions. The question mark matches any single character and asterisk matches any number of characters. However, a single asterisk will match only one folder.
For example, D:\CPP*\Build will not match either D:\CPP\MyProject\Ninja\Build or D:\CPP\MyProject\VS\Build. To match these folders, you have to use two asterisks like so D:\CPP**\Build.
Another limitation is that Wildcards cannot be used for the drive name.
warning: In newer versions of Windows 10, it is not possible to add Wildcards using the main Windows Security GUI. You have to use either PowerShell or Group Policy. For adding exclusions using these methods, see the relevant sections below.
Process Exclusions
As mentioned before, process exclusions exclude all files opened by a process from real-time protection. For specifying a process exclusion, you could supply the name of the executable or the full path. If only the name is specified all process with that name is excluded regardless of where they are located. Wildcards can be used here as well, but there are some additional restrictions. Wildcard:? is not allowed. Wildcard:* is allowed but must appear at the end of the path. Specifying the full path is the safest option.
Where is it useful?
Process exclusions can be useful if you have a trusted process that needs to open a large number of files. Windows Defender can become a severe drag on the performance of these types of processes. Real-time protection is triggered every time a process opens or closes a file. That is unless Windows Defender considers the file type or the process to be safe. Windows Defender is especially cautious about executable files. Windows defender checks a file whenever a file open call is made by a process and when a file close call is made by a process. This is going to take a lot of time if a process opens and closes a lot of files.
An Example
In my case, Windows Defender caused severe performance degradation of Find and Run Robot(FARR). FARR is an application launcher. Why would Windows Defender cause performance problems in an application launcher? It is because FARR opens matching files to extract their icon, for displaying in the search results.
If you are convinced that a process is safe you can add a process exclusion for it. Please note that only some special processes need process exclusion.
Using Powershell to add exclusions
You can use Powershell to add exclusions to Windows Defender. Please note that Powershell must be run as administrator. Here are some of the Windows Defender related commands available in Powershell.
1# Add exclusions
2# add a path to exclusion list
3Add-MpPreference -ExclusionPath E:\CPP
4# add a process to exclusion list
5Add-MpPreference -ExclusionProcess "C:\Program Files (x86)\FindAndRunRobot\FindAndRunRobot.exe"
6# add an extension to exclusion list
7Add-MpPreference -ExclusionExtension ".jpg"
8
9# Remove exclusions
10# remove a path from exclusion list
11Remove-MpPreference -ExclusionPath E:\CPP
12# remove a process from exclusion list
13Remove-MpPreference -ExclusionProcess "C:\Program Files (x86)\FindAndRunRobot\FindAndRunRobot.exe"
14# remove an extension from exclusion list
15Remove-MpPreference -ExclusionExtension ".jpg"
16
17# Display exclusions
18Get-MpPreference | Select-Object ExclusionProcess
19Get-MpPreference | Select-Object ExclusionPath
20Get-MpPreference | Select-Object ExclusionExtension
Verifying exclusions
You could verify that your exclusions are actually working with the help of an EICAR test file. This is a file developed by the European Institute for Computer Antivirus Research (EICAR) and Computer Antivirus Research Organization (CARO). The file is safe but it would trigger a response from all compliant AntiVirus software as per common consent among Antivirus makers. The purpose of the EICAR file is to test how an Antivirus reacts to a virus, whether an Antivirus can detect a virus inside a compressed archive etc. You can read more about it here
http://www.eicar.org/86-0-Intended-use.html
https://en.wikipedia.org/wiki/EICAR_test_file
EICAR is a simple text file with the following content X5O!P%@AP[4PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*. We can use this file to test if our exclusions are actually working. For example, to test if a folder exclusion is working create an EICAR file inside the folder; if the exclusion is working you will not see any Antivirus warning.
1cd D:\ExcludedFolder
2echo X5O!P%@AP[4\PZX54(P^^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H* > sample.txt
To test an extension exclusion you could create the EICAR file with the excluded extension instead of txt extension. For example, to test an exclusion for jpg files create an EICAR file with a jpg extension.
1echo X5O!P%@AP[4\PZX54(P^^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H* > sample.jpg
Using group policy to configure exclusions
You could also use group policy to configure exclusions.
Run gpedit.msc
Computer Configuration ➾ Administrative Templates ➾ Windows Components ➾ Microsoft Defender Antivirus➾ Exclusions
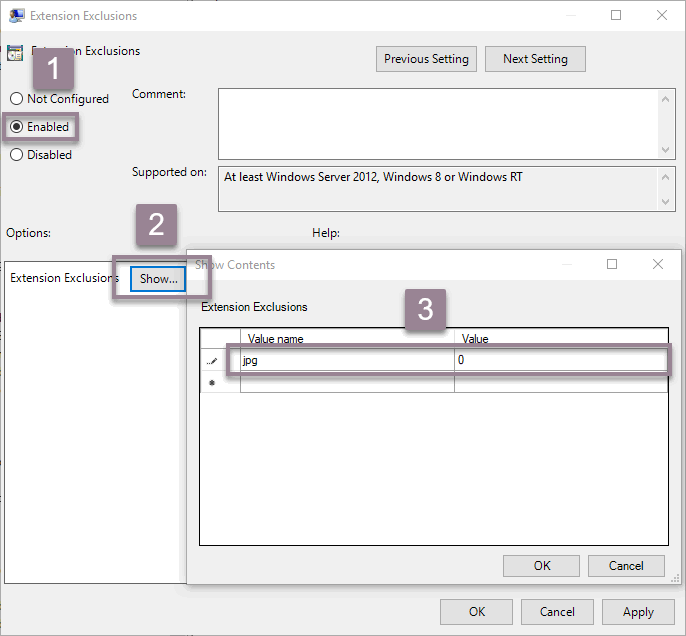
In order to add an exclusion double-click on the type of exclusion you want, select the Enabled radio button, click the Show button and add the exclusion in the new window which pops up. Exclusions must be added in the Value name column, the Value column must be set to 0.
Changes made to exclusions using Group Policy would show up in the exclusion list of Powershell and Windows Defender GUI. However, changes made by Powershell or Windows Defender GUI affect only the local policy. They will not show up in the Group Policy Editor. If there is a conflict between group policy and local policy exclusion settings, group policy settings would override local policy settings.
If you find that exclusions you have added using Windows Defender GUI or PowerShell are not having any effect, this could be the reason. An option to watch out for is Microsoft Defender Antivirus ➾ Configure local administrator merge behavior for lists in group policy. If this option is disabled on your computer, the exclusions you add to the local policy will not have any impact.